You may have heard about the Heartbleed OpenSSL Vulnerability issue and we wanted to be sure to address it directly. Although this is a serious security risk, Varsity is not aware of any specific affect it could have for the internal systems in your organization. We wanted to be sure to provide the specific details of the issue below.
While this is a very serious exploit, this does not affect your business critical systems (Servers, VPN, Email, etc.). OpenSSL is used primarily on Linux/Unix based computers using OpenSSL libraries (and specific versions of it) for encryption/cryptographic services. This is not a flaw with SSL/TLS protocols or any certificates used for secure communications on websites. Rather, this is an implementation problem with how the vulnerable OpenSSL libraries have been configured/programmed. Fortunately through conservative choices in equipment and software, this should not affect your corporate systems.
This could, however, affect you in other ways, as Linux-based systems using OpenSSL are used to encrypt usernames, passwords, and other sensitive information on many mainstream websites. Your popular social site, commerce site, hobby site, site you install software from, or even sites run by your government might be using vulnerable OpenSSL. Many major sites are already running fixed versions of OpenSSL and are already secure, however, some may take longer to be fixed.
It is also possible that your company’s website or hosting provider might be using the vulnerable OpenSSL version, but depending on the types of services used on a company website (for example if users have a secure login), it might or might not affect you. However, it is always best to proceed with caution and contact the hosting provider directly if you have any questions pertaining to your account/site security.
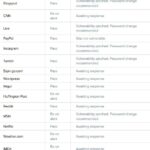
Below is a list of major sites that have been tested or are in the process of being tested, and some further explanation of the fixes being implemented:
Vulnerability patched. Password Change Recommended: The problem was fixed, but your password should be changed just in case.
Was not Vulnerable: The site was not using the version of OpenSSL encryption this bug was based on, and so was not vulnerable.
Awaiting Response: Still awaiting further testing to determine vulnerabilities.
Please click on the table below to enlarge it.
We will be providing updates as we receive them and hope this has provided some clarity.